Businesses today operate with significantly larger and more complex networks than ever before. BYOD policies, SaaS applications and hybrid/remote workforces have further propelled this paradigm shift. All of this makes it a challenge for both IT professionals and MSPs as they struggle to gain the required visibility into the IT environments of their organizations and clients respectively. However, with network discovery, you can turn this challenge into an opportunity.
But first, let’s understand what network discovery is, its importance in today’s IT landscape and how you can track your IT environments more effectively.
What is network discovery?
Network discovery allows administrators to gauge the devices connected to a network and how they interact with each other. System administrators often use it to map and monitor their network infrastructure. Network discovery makes it easy to locate devices in a network and share resources between them.
It also enables sys admins to locate devices easily on a large network, build device inventories, implement or improve device-access policies and most importantly, gain better control over the network. Essentially, it provides a complete view of a client’s IT network.
What is a network asset?
A network asset refers to any data, device or other component of an IT environment. Network assets generally fall under three categories — hardware, software and mission-critical information. Assets include:
- Routers
- Hubs
- Switches
- Firewalls
- Printers
- Hosts
- Servers
- Wireless access points
- Operating systems
- Applications
- Support systems
- Patches and updates
- Stored and managed data
What is the purpose of network discovery?
Network discovery helps in the creation of network maps that, in turn, improve the visibility of an IT environment. It enables enterprise IT teams to gain better control over their ever-expanding network and proves beneficial for rapidly growing small to midsize businesses (SMBs) as well. Due to their restricted internal IT teams, SMBs often struggle to keep track of new assets being added to their networks. Therefore, they turn to network discovery.
Why is network discovery important?
Without concrete knowledge of the network assets, the relationships between them and the way they communicate with each other, it’s impossible for an IT team to fully understand the network. The lack of comprehensive understanding of a network makes it a herculean task to deduce what went wrong in the event of downtime or interruption.
The sudden surge of hybrid work has made it increasingly difficult for businesses to identify issues. Network discovery helps in tackling this challenge as it brings to light all network assets and connections.
IT professionals can no longer just monitor basic performance metrics to guard a network’s integrity. Network discovery tools help investigate internal activity on a large and dynamic network.
Network discovery tools can help IT teams locate and map IP addresses accurately, and therefore, detect IP addresses that must be scrutinized and secured. Regular network discovery scans can also detect open ports on a network’s connected devices. Any unnecessary open ports can be a potential vulnerability. By effectively locating and mapping a network’s ports, network discovery helps IT professionals secure the network from port-related threats.
How does network discovery work?
Let’s now look at the role discovery protocols play in the entire process. IT teams utilize three primary discovery protocols:
- **Simple Network Management Protocol (SNMP):**IT teams use SNMP, an internet standard protocol, to collect and organize data about the assets on a network.
- **Link Layer Discovery Protocol (LLDP):**A vendor-neutral protocol, LLDP makes a device transmit information at scheduled intervals to another device it’s directly connected with. The recipient devices store this data in management information databases (MIBs) that can be accessed by IT teams.
- **Ping:**Ping is a software utility that IT teams utilize to test the reachability of devices on an IP network. During the process, internet control message protocol (ICMP) queries are sent, and the round-trip time of the messages sent from the host to a destination device is measured.
What does autodiscovery mean?
Autodiscovery is the process of automatically gathering data on network assets without the need for any manual input. For example, MSPs can use a remote monitoring and management (RMM) tool as an autodiscovery tool to locate devices, view device details, verify connection logs and monitor their overall performance.
What is a network discovery tool?
Network discovery tools use different discovery processes (discussed above) to create and maintain an inventory of network assets — empowering IT teams to better understand their networks. These protocols discover and gather information about:
- Virtual computers and networks
- A network’s hardware
- A network’s software
- The relationships between network assets
These tools gather this data by running IP scans, using ping sweeps and polling devices with SNMP monitoring. Some tools offer the capability to automate the entire process as well.
Active discovery tools
An active discovery tool goes across a network and pings each device it comes into contact with — the classic ping-and-response process. Active discovery could also use discovery tools that attempt to log in to assets to obtain a full inventory of connected applications.
However, active methods of network discovery can slow down a network due to all the contact attempts broadcast to the devices — a clear problem for time-sensitive networks like an industrial control system (ICS).
Passive discovery tools
Passive network discovery tools eliminate the consumption of network bandwidth since they gauge the traffic being broadcast around a network. However, it does require all devices to be able to send syslogs. This process involves collecting a log message and storing it in a log management solution. This data is updated regularly by the log management solution. It allows businesses to create assets from both live and historical data and allows them to retrieve data from various sources such as archived syslog messages.
Complete network discovery with RapidFire Tools
The growing importance of network discovery in today’s IT landscape is a golden opportunity. Besides gaining increased control of their infrastructure, IT professionals get equipped with the necessary knowledge to convince the senior leadership to increase the budget allocations. Also, MSPs can boost recurring revenue by using automation to offer clients ongoing network discovery and documentation services.
Network Detective Pro is the industry-leading IT assessment tool that goes beyond network discovery and documentation to provide real “value-added intelligence.” Its proprietary data collectors compare multiple data points to uncover hidden issues, measure risk, provide recommended fixes and track remediation progress.
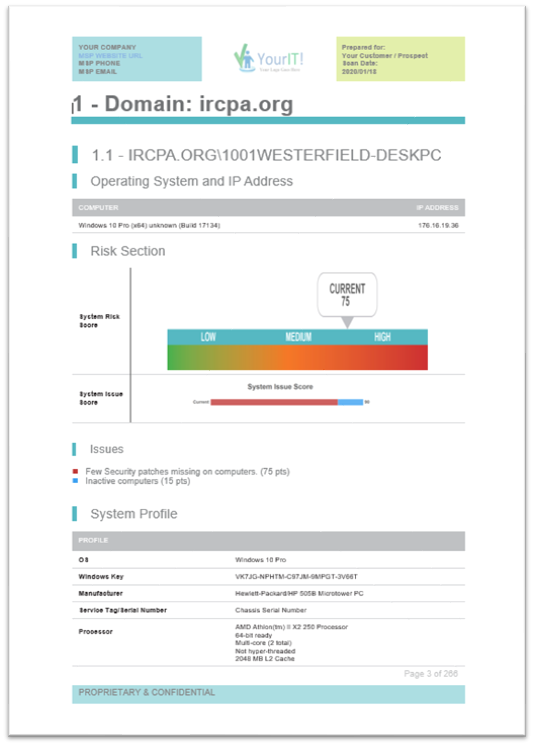
Using Network Detective Pro, you get access to brandable reports such as an Asset Detail Report. For each network scan, it provides detailed information on each individual asset discovered by Network Detective Pro. The report is ideal for cataloging and documenting the complete settings and configurations for individual workstations and servers.
Schedule a one-on-one demo so you can see the real power of Network Detective Pro for yourself.
