Reduce Risk with Network Scanning, Vulnerability and Continuous Compliance Management Solutions.
Automate Your IT Risk Management and Compliance Process
Four integrated tools working with you to protect the networks you manage.
Comprehensive Data Collection
Collect data from anywhere in your environment
In the cloud, on prem, and remote locations
Multiple scanner types available
Computers, networks, servers, cloud, end-users
Set-it and forget-it automated scheduling
Wizard-driven configuration guides make it easy
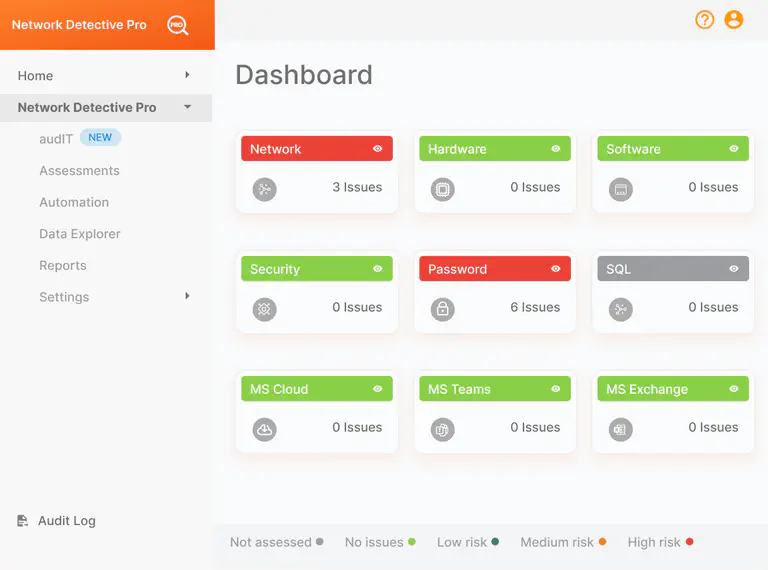
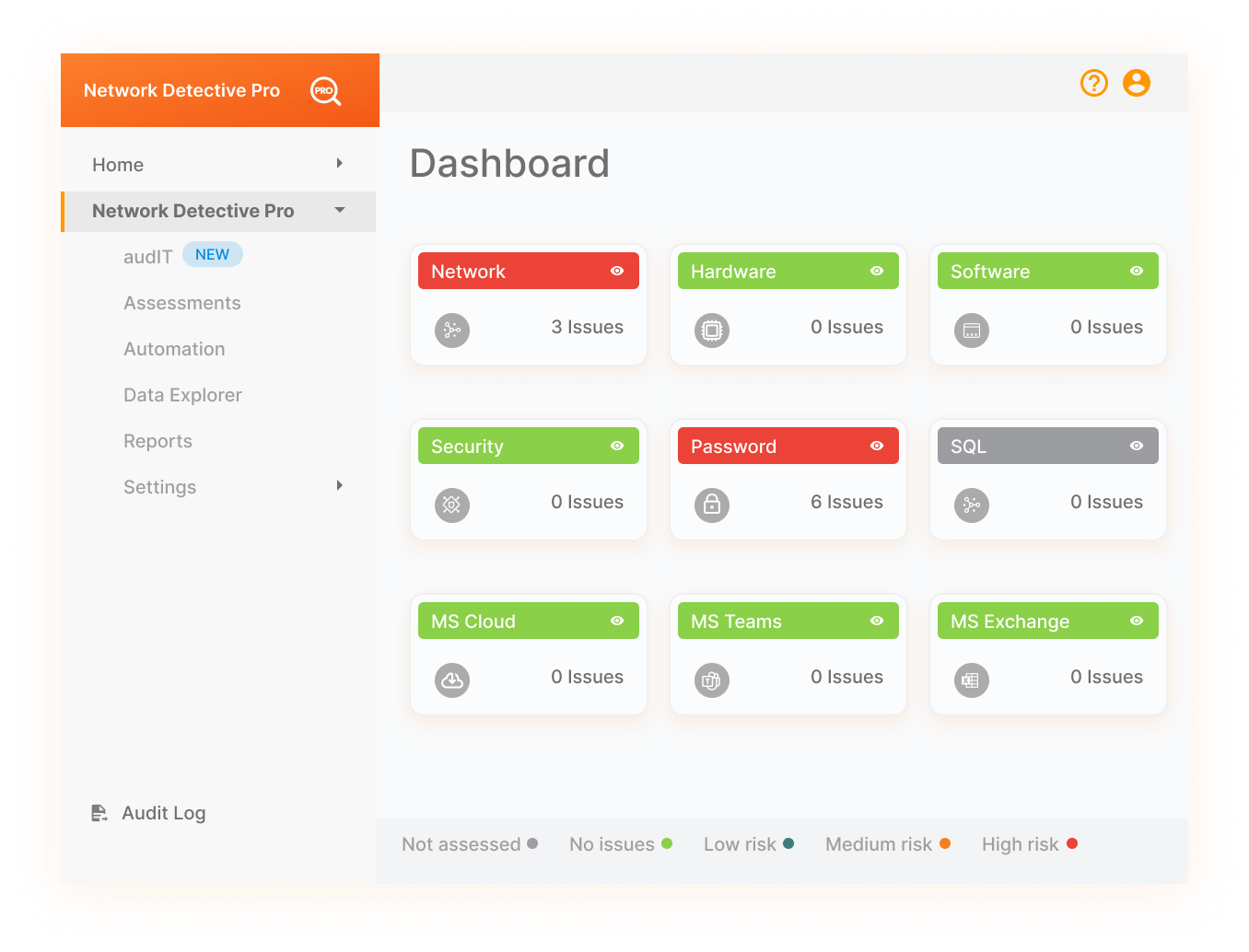
Automated Analysis and Risk Scoring
Data from all sources are automatically organized
Combined data is analyzed to highlight issues
All risks and issues are categorized and scored
Prioritize work based on issue and risk severity
Expert remediation guidance included in results
Resolve issues faster to reduce risk
Hundreds of Data-Driven, Brandable Reports
Wide range of IT assessment reports
Organized by assessment type, use and audience
Choice of report output formats
Dashboards, infographics, manuals, evidence, export files
Full compliance documentation
Dynamically generated based on each standard
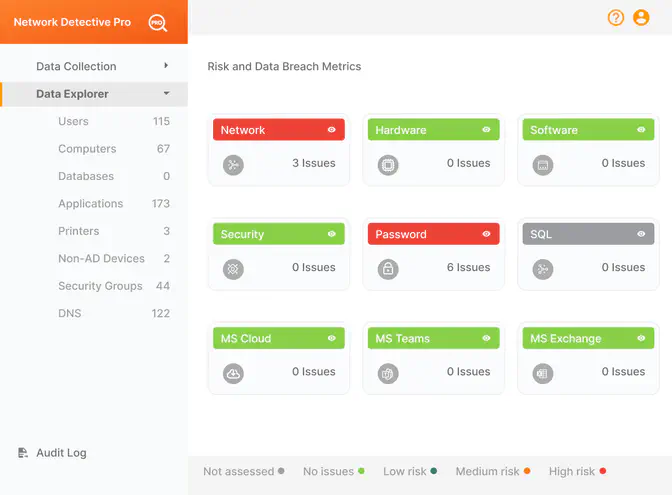
Network Detective Pro + audIT
Address hidden issues with automated IT assessments
Improve network visibility and uncover issues missed by other applications. Automatically collect data from every device, then generate actionable and compelling reports and presentations at the push of a button.
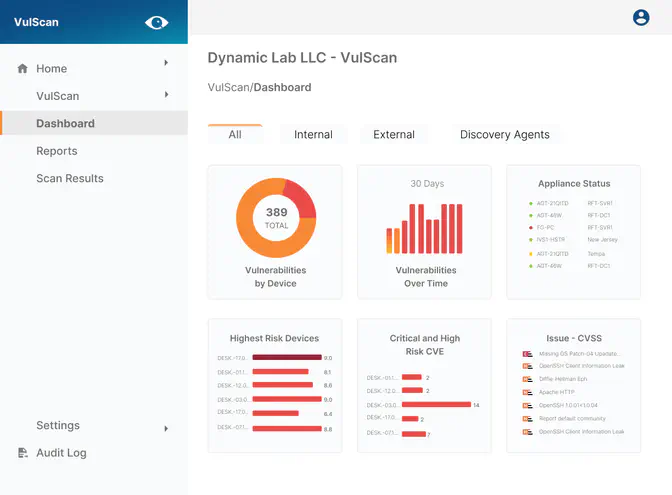
VulScan
Identify known vulnerabilities to reduce risk and liability
Effectively harden your entire IT environment against known vulnerabilities without all the complexity. Detect and prioritize issues quickly with automatic risk scoring and remediation suggestions.

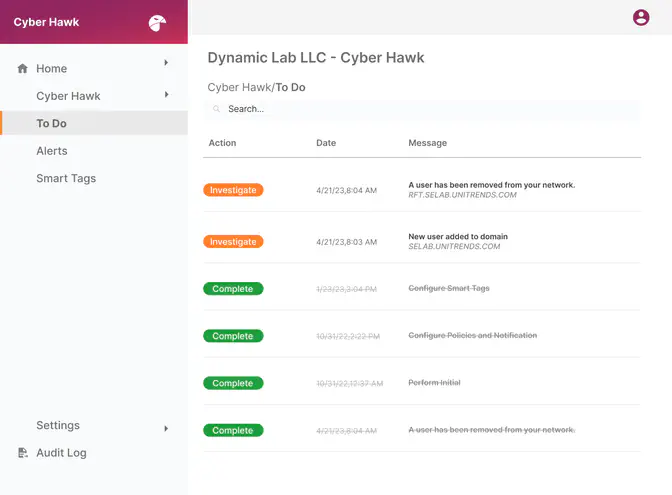
Cyber Hawk
Detect critical unauthorized and unplanned IT changes
Avoid the negative consequences of unplanned or unauthorized changes in your IT environment. Catch unauthorized log-in attempts, track suspicious changes to network settings, and identify anomalous user behavior.

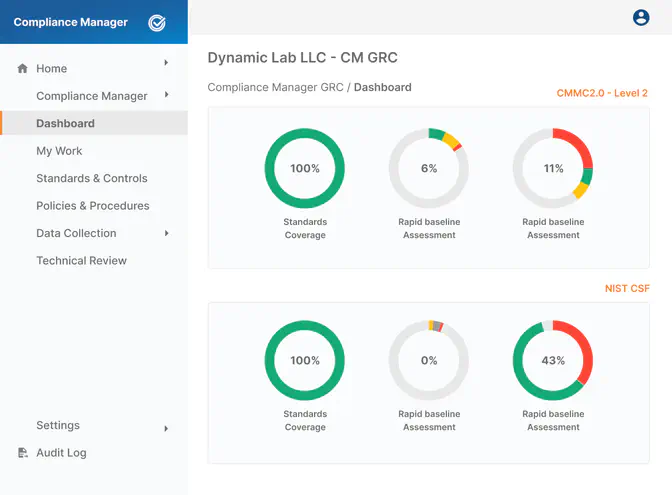
Compliance Manager GRC
Compliance, Simplified!
You're responsible for meeting IT compliance requirements from laws, industry standards and vendors. When audits or breaches happen, you need proof. Compliance Manager GRC continuously tracks requirements, monitors security, identifies risks and generates compliance reports — effortlessly.

Immediate access to your software after purchase
One log-in gets you instant access to any of our products.
24/7 support whenever, wherever needed
Chat directly with our friendly and knowledgeable product support specialists.
Continuous innovation at a rapid pace
Expect monthly updates with new features and innovations.
Up to 30% cost savings across entire stack
The more tools you buy, the more you save.
MSPs
Win new business, expand client relationships, and drive recurring revenue with comprehensive risk management and compliance services. Protect your clients better while earning a greater share of their IT spending.
Explore SolutionsIT Departments
Foster safer, more compliant operations with automated, data-driven IT assessments. Measure risk to optimize and secure your organization.
Explore Solutions