Automated GRC Software to Simplify Managing IT Compliance Regulations
Reduce the risk, complexity and costs associated with your InfoSec and IT compliance programs. Compliance Manager GRC software helps you manage any government regulation, industry standard or internal IT policy in one automated tool.









Simplify Governance, Risk Management and Compliance (GRC) for Any Organization
Compliance Manager GRC helps you identify which IT security requirements your organization should be following to stay compliant with any government or industry standard, and to reduce the risk of a data breach.
Automate your IT compliance management
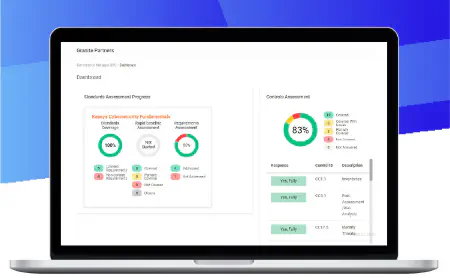
Save time and effort by automating a wide range of compliance assessment and management tasks. Easily collect data on users, computers and networks to validate compliance assumptions. Automatically show progress against the standards you are tracking.
Customize governance and compliance management to your needs
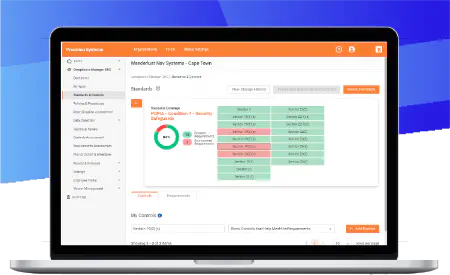
Manage multiple compliance standards at the same time in one centralized platform. Work from built-in compliance templates that you can modify or build your own standards from scratch with your specific controls and procedures.
Deliver dynamic reports and documentation
Eliminate fire drills by automatically generating comprehensive evidence of compliance in the event of an audit. Instantly produce up-to-date policies and procedures manuals, risk analysis reports, plans of action and supporting documents.
Continuous Compliance Monitoring
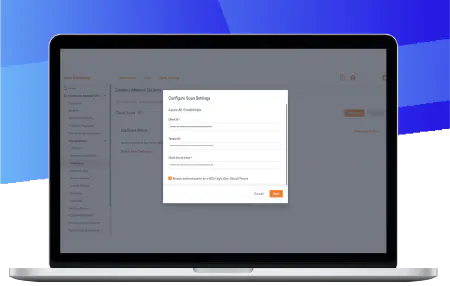
Compliance doesn’t stop at an audit — it’s an ongoing process. The Compliance Monitor feature continuously scans, assesses and monitors Microsoft Windows device configurations to determine whether the endpoints are configured to meet the Center for Internet Security (CIS) Benchmark configurations and selected IT Security Framework and Regulatory standards.
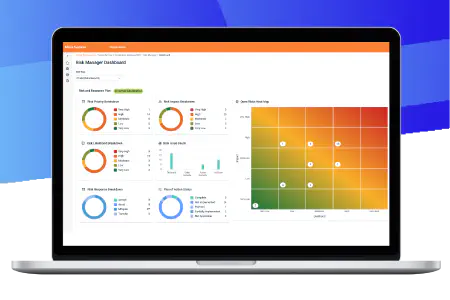
Manage Risk With Confidence
Risk Manager provides a centralized view of IT security, data security and compliance risks. It allows users to assign risk priorities, develop responses and create treatment plans to streamline the risk management process and address security and compliance lapses more efficiently. This feature empowers IT and security teams to make informed decisions faster while ensuring regulatory compliance and security best practices.
See How Compliance Manager GRC Works
Ensure compliance with IT requirements mandated by government laws and regulations, industry standards, vendor contacts and cyber insurance policies. Be ready with documented proof of compliance in the event of a forensic investigation or lawsuit following a breach.
Compliance Manager GRC keeps track of all your IT requirements, highlights issues and gaps that need your attention, and makes it easy to generate the reports and evidence of compliance whenever you need it.
Take interactive tourIT Security Assurance and Compliance Features
Compliance Manager GRC gives you a simple workflow process to keep track of all your IT requirements, regardless of source. Even if you are not regulated by a government or industry standard, you can still keep track of your own IT security and privacy requirements. With Compliance Manager GRC you can make sure you're doing the right things and doing them right.
Compliance Monitor
Continuously scan, assess and monitor Microsoft Windows device configurations to determine whether the endpoints are configured to meet the Center for Internet Security (CIS) Benchmark configurations and selected IT Security Framework and Regulatory standards.
Risk Manager
Get a centralized view of IT security, data security and compliance risks with a dynamic, actionable dashboard. This feature empowers IT and security teams to make informed decisions faster while ensuring regulatory compliance and security best practices.
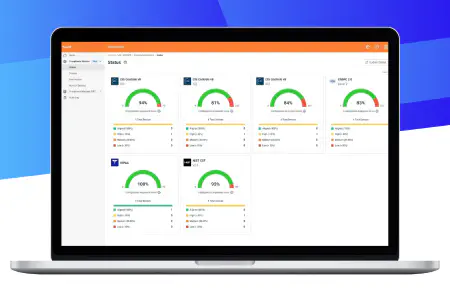
Supports all major standards and frameworks
Assess your compliance for the most common standards such as NIST CSF, HIPAA, PCI, CMMC, SOC 2, GDPR and many more. See All Standards Here.
Fully automated process management
Automatically collect data, generate risk assessments, create dynamic plans of action and produce evidence of compliance.
Third party vendor assessments
Easily manage the compliance requirements of your vendors with a built-in self-service portal. Make it easy for third parties to complete assessments against any standards you pick.
Built-in end user training, tracking and reporting
Train and test users on IT security awareness to reduce risk. Track and report on user training participation and attestation to policy documents.
Role-based architecture
Share the workload and responsibility of meeting specific requirements with the appropriate subject-matter experts.
Customizable libraries of controls and requirements
Large libraries of controls and requirements are included. You can easily modify them to create your own standards.
Tracks common controls across multiple standards
Eliminate duplication of effort managing the same control for multiple requirements in different standards.
Workflow integration with other Kaseya products
Automatically collect evidence from other software tools through seamless workflow automation.
Improve Your IT Compliance Processes With the Right Software
With the growing importance of GRC, it is vital to implement the right tool for your organization. In this buyer's guide, learn about the essential features to look for to manage the IT security standards you are tasked with supporting.
Download Now
Automated IT Compliance Reports
Compliance Manager GRC makes it easy to document your work with brandable and customizable reports. Select the documentation you need from an extensive library of templates.
Risk assessment reports
Quickly generate reports for any baseline assessment, controls assessment or requirements assessment.
Policies and procedures
Generate standard-specific policies and procedures manuals that you can customize based on how you work.
Supporting documents
Data-driven worksheets, check lists, inventories and other documents are automatically created during the assessment process.
Specialty reports
Specialty reports that are unique to a specific government regulation or industry standards are included.