Automated Network Scanning and Reporting Made Fast and Easy
Automate data collection across the entire network and easily identify risks and issues with Network Detective Pro. Transform complex IT assessment scan data into actionable reports and presentations for sales pitches and compliance reporting.


Make Your Network Assessments Tell the Perfect Story
Enhance network visibility and gather data from across the IT environments you manage. With Network Detective Pro you can uncover, prioritize, and manage risks and issues. This cloud-based platform saves time, improves client retention, and seamlessly delivers both technical insights and business reports.
Improve issue discovery with automated network scanning
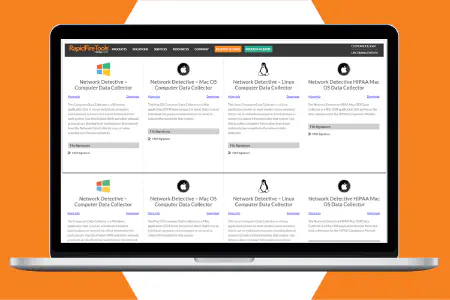
Ensure the integrity of your systems with automated data collectors. Network Detective Pro uses non-intrusive data collectors, light-weight discovery agents, and powerful scanners to identify risks quickly.
Respond to incidents and troubleshoot with speed
Reduce risk efficiently with detailed management plans and remediation guidance that scores network threats and issues based on severity. Customize which IT issues are reported and the importance that they are given in an assessment.
Show value with executive and technical reporting
Gain insights with automated reports. From technical reports for documentation and troubleshooting, to high level summaries for executive presentations. Demonstrate your value to any IT stakeholder.
See How Network Detective Pro Works
Staying ahead in the rapidly evolving IT landscape is crucial. Network Detective Pro elevates your network management capabilities by providing an advanced platform for comprehensive network analysis and risk assessments. Network Detective Pro goes beyond traditional IT assessments by offering automated, real-time data collection and analysis across various network environments.
Whether dealing with on-premises, cloud-based, or hybrid systems, this tool ensures you have a complete and current view of your network's health and security posture. Its sophisticated algorithms automatically identify and score risks, enabling you to prioritize your response efficiently. Experience the seamless integration of technical risk assessments, remediation planning, service ticket automation, and executive reporting in one intuitive platform. And now with audIT integrated into Network Detective Pro, generate prospecting and sales presentations automatically with the data you’ve collected
Take Interactive Tour Try Network Detective ProPowerful Features for Your Network Scanning and Assessments
Network Detective Pro is a comprehensive solution that provides deep insights into your network infrastructure. Its innovative and powerful capabilities allow you to easily gather information and monitor your network's health, vulnerabilities, and performance.
New Reporting Engine powered by audIT
It’s the best of both worlds! Network Detective Pro and audIT are now integrated to give you the fastest, easiest and most comprehensive network assessment and reporting solution.
MSPs: Learn MoreFull coverage network scanning
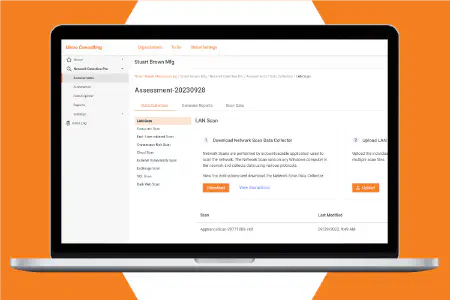
Gain increased network visibility through the most comprehensive network scanning techniques. Such as non-intrusive scans on Windows, macOS and Linux, as well as remote data collectors and light-weight discovery agents.
Multiple network assessment types
Reduce risk across multiple threat vectors with a variety of assessments. Focus your assessments on networks, security, cyberattack risk, MS-365 environments or SQL servers. Including Active Directory, Azure AD (Active Directory), AWS (Amazon Web Services) and more.
End-to-end scheduling and automation
Increase the efficiency and frequency of your assessments with automated data collection and analysis. Then Display insights with detailed reporting, while saving time and further minimizing risk.
Standard and proprietary risk scoring
Prioritize risks based on unique risk scoring algorithms as well as industry standard CVSS and Microsoft Secure Scores. Tackle the most important risks first, based on severity, likelihood of threat and impact on your organization.
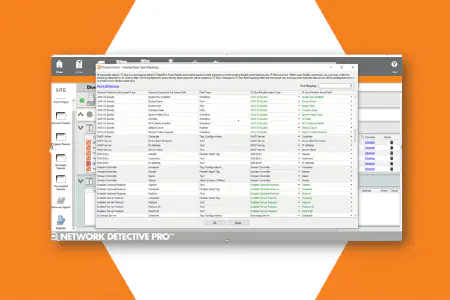
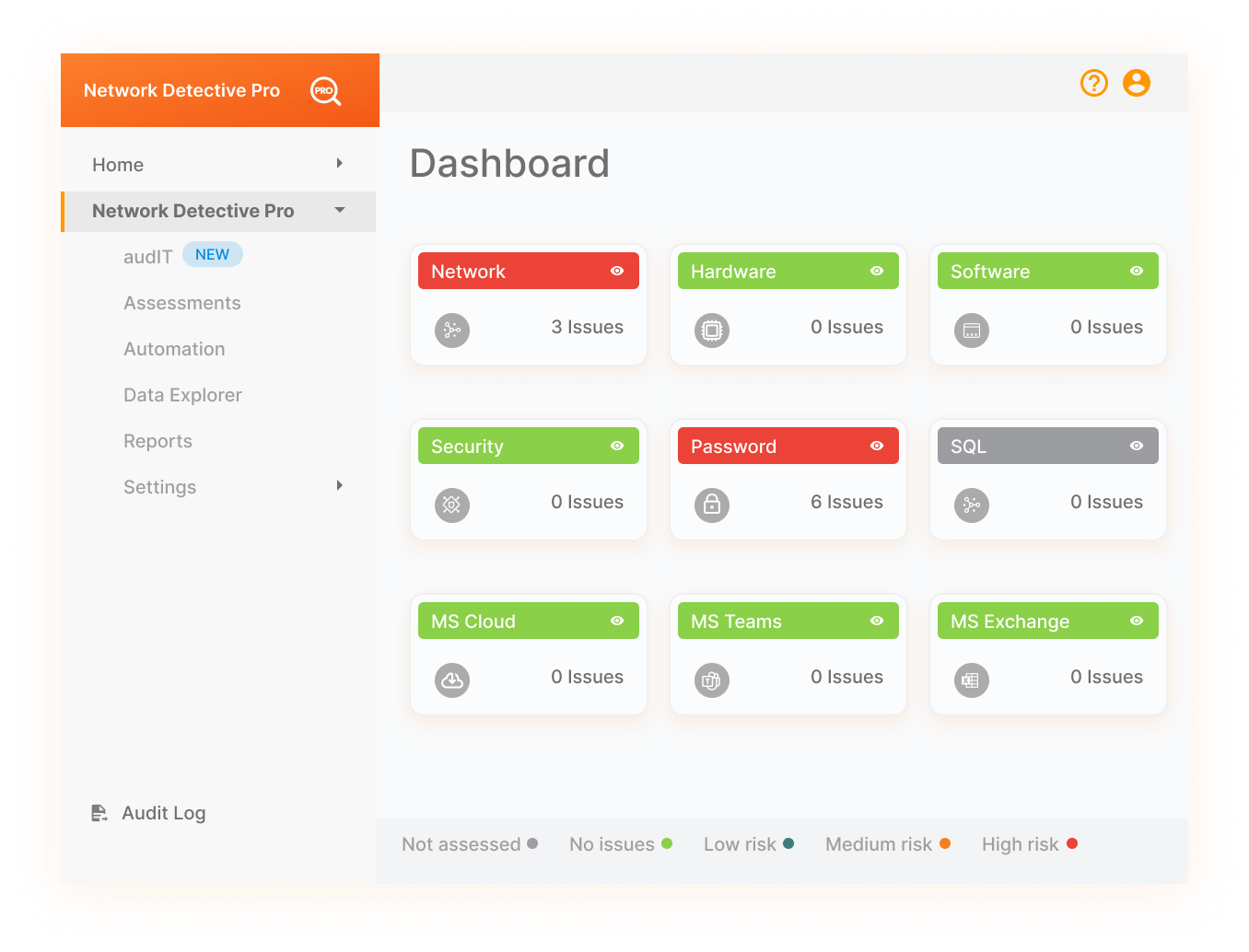
Online dashboard with drill-down data explorer
Save time by accessing all discovered data from anywhere, any time through the RapidFire Tools online portal. The dashboard displays the summary info you need. Then drill in for the details and guidance on any discovered risk or issue.
Workflow integrations with other applications
Seamlessly convert discovered issues into PSA service tickets, or into ITGlue for updated network documentation. Pull in data from VulScan, Dark Web ID, MS 365 and other apps to generate expanded reports.
Try Network Detective Pro's Cyberattack Risk Assessment feature
The Cyberattack Risk Assessment is a special feature that makes it extremely quick and easy to remotely spot-check computers on any network and look for hidden vulnerabilities that could be exploited by a successful phishing attack, malicious insider or hacker who has managed to breach your firewall.
Try It For Free
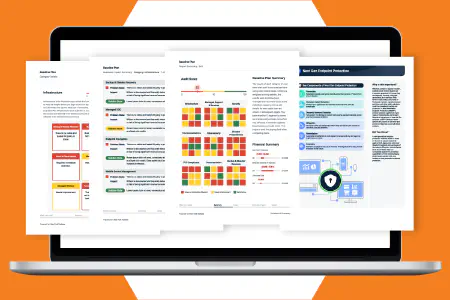
Automated Network Assessment Reports for Every Use Case
Network Detective Pro provides an extensive library of dynamic reports populated with the data from your network scans. The automated branding engine customizes the look and feel of the document to match your organization. Troubleshoot issues faster with technical reports and show key stakeholders the value of what you do.